Schedule a Live Demo Free 90-Day Trial Watch our Quick Demo
TRAIN TRACK® Cloud and Installed Editions (Client and Web interfaces) provide everything you need for Compliance with FDA 21 CFR Part 11. TRAIN TRACK® allows you to track changes,
control access, and prevent unauthorized changes through password protection, audit trails, and electronic signatures.
TRAIN TRACK® is designed to meet all of your documentation requirements for quality standards such as ISO 9001, ISO 13485,
AS9100, TS 16949, ISSA CIMS, and SQF 2000, and is guaranteed to pass an FDA audit. A listing of applicable standards and regulations,
and how TRAIN TRACK® meets them, is included below.
Click here to learn more about how to conduct your own validation.
The data stored in TRAIN TRACK® is protected by system controls and multiple layers of security. This helps ensure the integrity of the records.
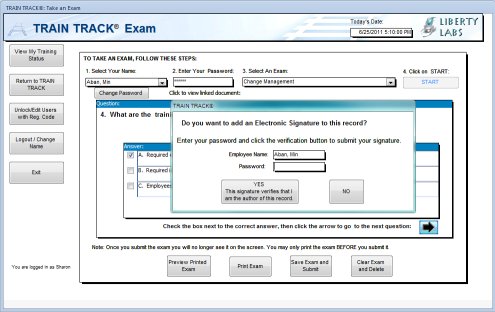
TRAIN TRACK® allows users to secure data with electronic signatures. The user enters their user name and password and confirms the record they wish to sign, and the meaning of the signature. Once the user confirms the decision to apply the signature, the entry is locked from further editing.
The chart below details the FDA requirements, and how each of them is met within the program.
Regulation |
Requirement |
Specification |
| 21CFR11 Part 11 Subpart B--Electronic Records Sec. 11.10 Controls for closed systems | (a) Validation of systems to ensure accuracy, reliability, consistent intended performance, and the ability to discern invalid or altered records. |
TRAIN TRACK® has been validated and the validation documents are available for purchase separately. |
| (b) The ability to generate accurate and complete copies of records in both human readable and electronic form suitable for inspection, review, and copying by the agency. Persons should contact the agency if there are any questions regarding the ability of the agency to perform such review and copying of the electronic records. |
All records, including the audit trail, may be exported to Excel®. | |
| (c) Protection of records to enable their accurate and ready retrieval throughout the records retention period. |
Records may be given a status of "inactive" which maintains them in the system but excludes them from views of current records. The audit trail records deletions. | |
| (d) Limiting system access to authorized individuals. |
Users must log in to TRAIN TRACK® using either their authenticated Windows® login, or a unique login ID and password. An Inactivity lock secures the program after a period of inactivity. |
|
| (e) Use of secure, computer-generated, time-stamped audit trails to independently record the date and time of operator entries and actions that create, modify, or delete electronic records. Record changes shall not obscure previously recorded information. Such audit trail documentation shall be retained for a period at least as long as that required for the subject electronic records and shall be available for agency review and copying. |
The audit trail provides a complete change history for each record:
TRAIN TRACK® allows you to view the audit trail records in a variety of ways, such as all changes for a specific training (changes in requirements, completions, etc.), or for a specific employee; all changes made by a specific user, or within a specific date range. These records may be exported to Excel®. |
|
| (f) Use of operational system checks to enforce permitted sequencing of steps and events, as appropriate. |
Data validation does not allow completion dates in the future to be entered. The user must select certain values from selection lists. TRAIN TRACK® controls the entry of document revisions and requires the user to indicate if re-training is required. | |
| (g) Use of authority checks to ensure that only authorized individuals can use the system, electronically sign a record, access the operation or computer system input or output device, alter a record, or perform the operation at hand. |
Multiple Levels of Security allow different parts of your program to be seen or updated by users with the appropriate credentials |
|
| (h) Use of device (e.g., terminal) checks to determine, as appropriate, the validity of the source of data input or operational instruction. |
User logins are captured in the audit trail. | |
| (i) Determination that persons who develop, maintain, or use electronic record/electronic signature systems have the education, training, and experience to perform their assigned tasks. |
Documentation of training completion is maintained within the system. | |
| (j) The establishment of, and adherence to, written policies that hold individuals accountable and responsible for actions initiated under their electronic signatures, in order to deter record and signature falsification. |
While the end-user's organization is responsible for these policies, the program also displays messages alerting the user to the appropriate use of electronic signatures. | |
(k) Use of appropriate controls over systems documentation including:
|
While the end-user's organization is responsible for these controls, Liberty Labs, LLC also adheres to a quality management and change control system, and the system is fully documented. | |
| 21CFR11 Part 11 Subpart B--Electronic Records Sec. 11.30 Controls for open systems. | Persons who use open systems to create, modify, maintain, or transmit electronic records shall employ procedures and controls designed to ensure the authenticity, integrity, and, as appropriate, the confidentiality of electronic records from the point of their creation to the point of their receipt. Such procedures and controls shall include those identified in 11.10, as appropriate, and additional measures such as document encryption and use of appropriate digital signature standards to ensure, as necessary under the circumstances, record authenticity, integrity, and confidentiality. | TRAIN TRACK® is not an open system. |
| 21CFR11 Part 11 Subpart B--Electronic Records Sec. 11.50 Signature manifestations. | (a) Signed electronic records shall contain information associated with the signing that clearly indicates all of the following:
|
The Client/Server and Web editions allow users to secure data with electronic signatures. The user enters their user name and password, and confirms the record they wish to sign, and the meaning of the signature. This record is stored with a timestamp generated by the system. Once the user confirms the decision to apply the signature, the entry is locked from further editing. Adding electronic signatures is captured on the audit trail. |
| (b) The items identified in paragraphs (a)(1), (a)(2), and (a)(3) of this section shall be subject to the same controls as for electronic records and shall be included as part of any human readable form of the electronic record (such as electronic display or printout). | Displays and reports with electronic signatures include all required elements:
|
|
| 21CFR11 Part 11 Subpart B--Electronic Records Sec. 11.70 Signature/record linking. | Electronic signatures and handwritten signatures executed to electronic records shall be linked to their respective electronic records to ensure that the signatures cannot be excised, copied, or otherwise transferred to falsify an electronic record by ordinary means. | Electronic signatures are stored as part of the record for the training completion. They are linked to the record by being stored as part of the record. When a signature is applied, the training completion record is edited to include that signature. Applying an electronic signature is recorded in the audit trail. |
| 21CFR11 Part 11 Subpart C--Electronic Signatures Sec. 11.100 General requirements. | (a) Each electronic signature shall be unique to one individual and shall not be reused by, or reassigned to, anyone else. | Each signature is associated with a unique employee record in the database. A unique ID number is assigned to each record. |
| (b) Before an organization establishes, assigns, certifies, or otherwise sanctions an individual's electronic signature, or any element of such electronic signature, the organization shall verify the identity of the individual. | The end user is responsible for verifying the identity of each employee prior to assigning a signature. | |
| 21CFR11 Part 11 Subpart C--Electronic Records Sec. 11.200 Electronic signature components and controls. | (a) Electronic signatures that are not based upon biometrics shall:
|
Electronic signatures always require a user name and password. Each user name and password is linked to an employee record, containing additional data about the employee. |
| (b) Electronic signatures based upon biometrics shall be designed to ensure that they cannot be used by anyone other than their genuine owners. | TRAIN TRACK® does not use biometrics. | |
| 21CFR11 Part 11 Subpart C--Electronic Records Sec. 11.300 Controls for identification codes/passwords. | (a) Maintaining the uniqueness of each combined identification code and password, such that no two individuals have the same combination of identification code and password. |
Each user name and password must be unique. |
| (b) Ensuring that identification code and password issuances are periodically checked, recalled, or revised (e.g., to cover such events as password aging). |
Password expiration periods may be set by the program administrator, or passwords expire in 120 days. | |
| (c) Following loss management procedures to electronically deauthorize lost, stolen, missing, or otherwise potentially compromised tokens, cards, and other devices that bear or generate identification code or password information, and to issue temporary or permanent replacements using suitable, rigorous controls. | TRAIN TRACK® does not use devices, such as tokens or cards. | |
| (d) Use of transaction safeguards to prevent unauthorized use of passwords and/or identification codes, and to detect and report in an immediate and urgent manner any attempts at their unauthorized use to the system security unit, and, as appropriate, to organizational management. |
Entering an incorrect password is captured on the audit trail. Repeated entry of incorrect passwords triggers an alert notification. | |
| (e) Initial and periodic testing of devices, such as tokens or cards, that bear or generate identification code or password information to ensure that they function properly and have not been altered in an unauthorized manner. | TRAIN TRACK® does not use devices, such as tokens or cards. |
Click here to view CFR - Code of Federal Regulations Title 21 (FDA Web site)
What are the training documentation requirements for SQF 2000?
SQF 2000 Code
Training Register Requirements:
6.3.7.1 A training skills register describing who has been trained in relevant skills shall be maintained. The register shall indicate the:
i. Participant name;
ii. Skills description;
iii. Description of the training provided;
iv. Date training completed;
v. Trainer or training provider; and
vi. Supervisor’s verification the training was completed and that the trainee is competent to complete the required tasks.
How does TRAIN TRACK® meet these requirements?
TRAIN TRACK® Employee training tracking application meets the training skills register requirements:
The application allows users to list required training, including a training title, number, and type, and attach a detailed document to each training record (ii, iii).
Users may designate qualified instructors for each training, and schedule classes led by the approved instructors (v).
The program allows users to document training completions for each employee, including the completion date and employee name (I, iv).
TRAIN TRACK® includes the ability to add an electronic signature to verify training completion records, and an audit trail of all record changes (vi).